PUBLIC KEY INFRASTRUCTURES in Nutshell
by Anish
Posted on Saturday August 11, 2018
Introduction
This sample chapter extracted from the book, The Modern Cryptograhy CookBook . The Book theme isCryptography is for EveryOne. Learn from Crypto Principle to Applied Cryptography With Practical Example
Get this book on Just $9 by availing coupon discount
A public key infrastructure (PKI) binds public keys to entities, enables other entities to verify public key bindings, and provides the services needed for ongoing management of keys in a distributed system
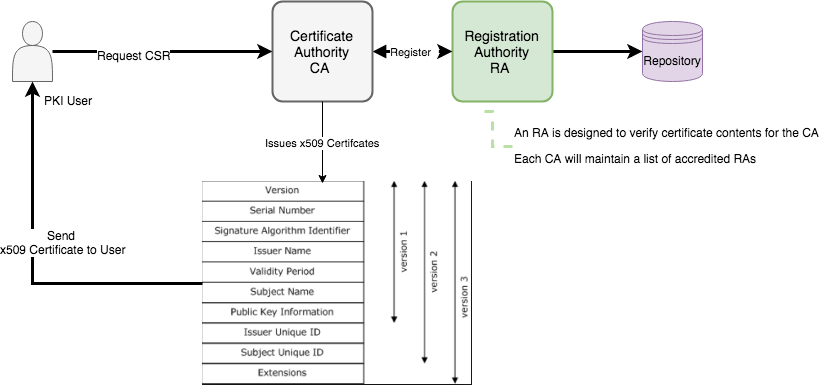
Certification Authority (CA)
The CA issues a public key certificate for each identity, confirming that the identity has the appropriate credentials.
Main Functions of CA
- Verify the CSR request
- Issue the Certificate (Create and SIgn them)
- Attach CRL for Certificate revocation
- Publish it’s current (Expired Certificate ) and CRL’s
Registration Authority (RA)
An RA is designed to verify certificate contents for the CA. Each CA will maintain a list of accredited RAs; that is a list of RAs determined to be trustworthy
PKI Users
PKI Users are organizations or individuals that use the PKI, but do not issue certificates.
Main Functions of PKI user
- Generate the Certificate Signing Request.
- Maintain the Certificate obtain by the CA.
PKI Architecture
CAs may be linked in a number of ways. Most enterprises that deploy a PKI will choose either a mesh or a hierarchical architecture, This is an example of hierarchical Structure
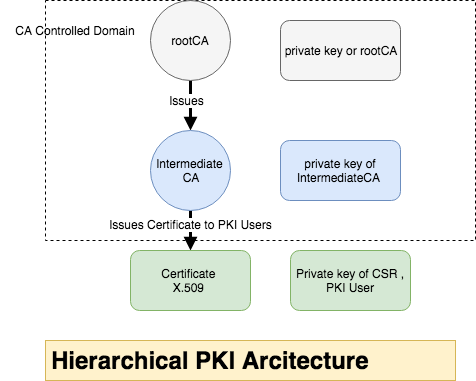
Generating hierarchical CA structure
-
rootCA will generate self signed certificate and key with longer validity
openssl genrsa -des3 -out rootCA.key 4096 openssl req -new -x509 -days 3650 -key rootCA.key -out rootCA.crt -
intCA will generate CSR and get it signed with rootCA and set Validity for Longer Year.
openssl genrsa -des3 -out intCA.key 4096 openssl req -new -key intCA.key -out intCA.csr
intCA Submited the CSR information to rootCA to get it signed
Enter pass phrase for intCA.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:KA
Locality Name (eg, city) []:IN
Organization Name (eg, company) [Internet Widgits Pty Ltd]:IntermediateCA Issuers
Organizational Unit Name (eg, section) []:intermediateCA Issue of myOrg
Common Name (e.g. server FQDN or YOUR name) []:intCA
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
-
Sign intermediateCA with rootCA private key, control the serial Number to specific pattern (Usability)
openssl x509 -req -days 365 -in intCA.csr -CA rootCA.crt -CAkey rootCA.key -set_serial 1111111 -out intCA.crt Signature ok subject=/C=AU/ST=KA/L=IN/O=IntermediateCA Issuers/OU=intermediateCA Issue of myOrg/CN=intCA Getting CA Private Key Enter pass phrase for rootCA.key: -
PKI (End)Users will create the CSR and send to CA to get it signed
openssl genrsa -des3 -out client.key 2048 openssl req -new -key client.key -out client.csr
End user submit the CSR information to get it signed by the CA, the CA used intermediate CA to sign the CSR
Enter pass phrase for client.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:My Org
Locality Name (eg, city) []:IN
Organization Name (eg, company) [Internet Widgits Pty Ltd]:8gwifi
Organizational Unit Name (eg, section) []:Crypto
Common Name (e.g. server FQDN or YOUR name) []:8gwifi.org
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
-
Sign with Intermediate CA,set the exipry date to 1 or 2 year Max, and generate a serial number for this
openssl x509 -req -in client.csr -days 530 -CA intCA.crt -CAkey intCA.key -CAcreateserial -out client.crt
The CSR getting signed
Signature ok
subject=/C=AU/ST=My Org/L=IN/O=8gwifi/OU=Crypto/CN=8gwifi.org
Getting CA Private Key
Enter pass phrase for intCA.key:
-
View the Client Certificate Information , The issuer is IntermediateCA
openssl x509 -text -in client.crt ....... ...... Signature Algorithm: sha1WithRSAEncryption Issuer: C=AU, ST=KA, L=IN, O=IntermediateCA Issuers, OU=intermediateCA Issue of myOrg, CN=intCA -
Verify Certificate
Verify Client certificate with Full CA chain
openssl verify -verbose -CAfile <(cat intCA.crt rootCA.crt) client.crt
client.crt: OK
Verify intermediateCA belongs to rootCA chain
openssl verify -verbose -CAfile rootCA.crt intCA.crt
intCA.crt: OK
PKI Data Structure
Two Basic data structures used in PKI
- X.509 Public Key Certificates
- CRL Certificate Revocation List
- Attribute Certificates
X.509
There are ten common fields, six mandatory and four optional.
The mandatory fields are: serial number, signature algorithm identifier, certificate issuer name, certificate validity period, public key Info , and the subject name
| X.509 Attributes | Description |
|---|---|
| Version | v2 or v3 |
| Serial Number | CA Assigned Serial Number to the Certificate |
| Signature | Indicate which digital Signature Algorithms ex: SHA-256 with RSA Encryption |
| Issuer | Contains x.500 DN |
| Validity | Certificate Expiry Dates |
| Subject | Contains the DN of the Holder of private Key Corresponding to the public key in the certificate |
| Subject public key Information | Optional Parameter, Algorithm Identifiers |
| Issuer UniqueID and Subject UniqueID | ID of the Issues only in v2 and v3 |
| Extensions | Optional only in v3 Certificate version |
| subjectType | Indicate whether a subject is CA or ENtity |
| Names and identity information | c=US; o=8gwifi; ou=Crypto; cn=8gwifi.org |
| Key Attributes | Specifies relevant attributes whether it used for key transport, or be used to verify a digital signature |
| Policy Information | Policies related to Certificate |
| Certificate Extensions | extension identifier, a criticality flag, and extension value |
Reader Note what is self Signed Certificate
In self signed certificate the issuer and subject are same :)
Issuer: C=AU, ST=KA, L=IN, O=rootCA Issuers, OU=rootCA, CN=rootCA
Subject: C=AU, ST=KA, L=IN, O=rootCA Issuers, OU=rootCA, CN=rootCA
CRL
The CRL contains the following fields:
| CRL Fields | Description |
|---|---|
| Version | Optional Version, Default 2 |
| Signature | algorithm identifier for the digital signature algorithm used by the CRL issuer to sign the CRL |
| Issuer | X.500 DN of the CRL issuer |
| This update | Issue date of the CRL |
| Next update | Next CRL Issue date |
| Revoked Certificates | Structured List of Revoked Certificates |
| CRL Extensions | Additional Information About the CRL |
Pem format of CRL
-----BEGIN X509 CRL-----
-----END X509 CRL-----
Implement CERTIFICATION REVOCATION LIST
-
Make a directory for a CRL:
mkdir -p /etc/pki/crl -
Create an index file, the CRL Database with the following command:
touch /etc/pki/crl/index.txt -
Create a file for the CRL number. This file should contain the text 00 only.
echo 00 > /etc/pki/crl/crl_number -
crl_openssl.conf: create and write the following contents into a crl_openssl.conf file.
cat <<EOF > crl_openssl.conf # OpenSSL configuration for CRL generation # #################################################################### [ ca ] default_ca = CA_default # The default ca section #################################################################### [ CA_default ] database = /etc/pki/crl/index.txt crlnumber = /etc/pki/crl_number default_days = 365 # how long to certify for default_crl_days= 30 # how long before next CRL default_md = default # use public key default MD preserve = no # keep passed DN ordering #################################################################### [ crl_ext ] # CRL extensions. # Only issuerAltName and authorityKeyIdentifier make any sense in a CRL. # issuerAltName=issuer:copy authorityKeyIdentifier=keyid:always,issuer:always EOF -
Generate CRL file
openssl ca -gencrl -keyfile intCA.key -cert intCA.crt -out intCA.crl -config crl_openssl.conf -
View CRL file
Added with required CRL field, at this time no certificate is Invoked
openssl crl -text -noout -in intCA.crl
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=AU/ST=Some-State/O=Internet Widgits Pty Ltd/CN=intermediateCA
Last Update: Aug 8 06:54:55 2018 GMT
Next Update: Sep 7 06:54:55 2018 GMT
CRL extensions:
X509v3 CRL Number:
0
No Revoked Certificates.
Signature Algorithm: sha256WithRSAEncryption
if the CRL is DER Encoded then issue the below command
openssl crl -inform DER -text -noout -in mycrl.crl
-
Revoke the Certificate
openssl ca -revoke client.crt -keyfile intCA.key -cert intCA.crt -config crl_openssl.conf Using configuration from crl_openssl.conf Enter pass phrase for intCA.key: Adding Entry with serial number AC12C39820C69327 to DB for /C=AU/ST=Some-State/O=Internet Widgits Pty Ltd/CN=8gwifi.org Revoking Certificate AC12C39820C69327. Data Base Updated -
Again revoking the same client certificate will through an error Already Revoked
openssl ca -revoke client.crt -keyfile intCA.key -cert intCA.crt -config crl_openssl.conf Using configuration from crl_openssl.conf Enter pass phrase for intCA.key: ERROR:Already revoked, serial number AC12C39820C69327 -
Regenerate the CRL list
openssl ca -gencrl -keyfile intCA.key -cert intCA.crt -out intCA.crl -config crl_openssl.conf Using configuration from crl_openssl.conf Enter pass phrase for intCA.key: -
View CRL file
One revoked certificate is Added in the CRL entry
openssl crl -text -noout -in intCA.crl
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=AU/ST=Some-State/O=Internet Widgits Pty Ltd/CN=intermediateCA
Last Update: Aug 8 07:08:08 2018 GMT
Next Update: Sep 7 07:08:08 2018 GMT
CRL extensions:
X509v3 CRL Number:
2
Revoked Certificates:
Serial Number: AC12C39820C69327
Revocation Date: Aug 8 07:01:07 2018 GMT
Adding CRL distribution point
-
Edit the file crl_openssl.conf and point out the PEM and DER
crlDistributionPoints=@crl_section [crl_section] URI.1 = https://8gwifi.org/intCA.crl URI.2 = https://8gwifi.org/intCA.der -
CA role , once CA sign the file it will use
-extfile crl_openssl.confto locate the crlDistributionPointsopenssl x509 -req -in client.csr -days 530 -CA intCA.crt -CAkey intCA.key -CAcreateserial -out client.crt -extfile crl_openssl.conf -
Once certificate is Signed, the x.509 certificate will have X509v3 extensions that contains CRL Distribution Points
openssl x509 -text -in client.crt ...... X509v3 extensions: X509v3 CRL Distribution Points: Full Name: URI:https://8gwifi.org/intCA.crl Full Name: URI:https://8gwifi.org/intCA.der
Continue Reading OCSP in Nutshell
Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Applied Cryptography Topics
Web Crypto API Topics
Ansible Related Topics
Kubernetes Related Topics
Openstack Articles
Linux Related Topics
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile