Overview of Linux Namespace
by Anish
Posted on Monday December 09/2019
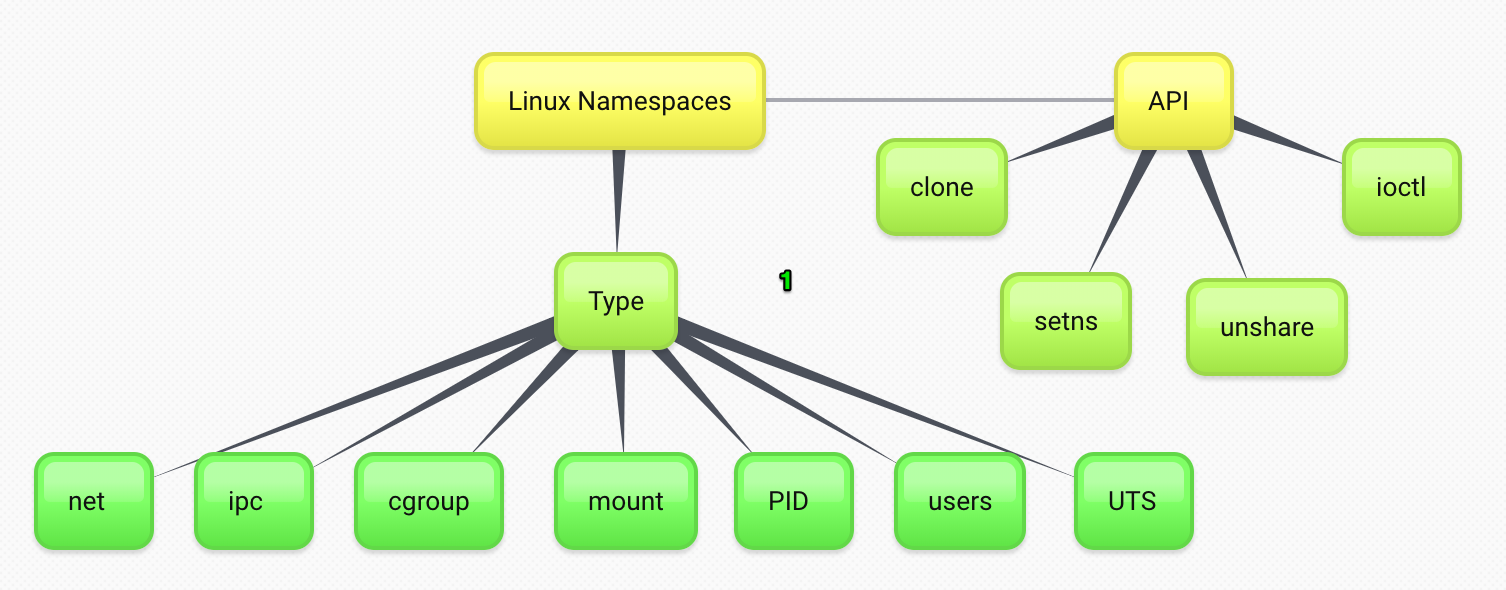
Namespace is Linux Kernel feature
A namespace wraps a global system resource in an abstraction that makes it appear to the processes within the namespace that they have their own isolated instance of the global resource. Changes to the global resource are visible to other processes that are members of the namespace but are invisible to other processes.
For more information, see the namespaces(7) man page.
Namespaces are specified as an array of entries inside the namespaces root field. The following parameters can be specified to set up namespaces:
Example
"namespaces": [
{
"type": "pid",
"path": "/proc/1234/ns/pid"
},
{
"type": "network",
"path": "/var/run/netns/neta"
},
{
"type": "mount"
},
{
"type": "ipc"
},
{
"type": "uts"
},
{
"type": "user"
},
{
"type": "cgroup"
}
]
The /proc filesystem shows (in the /proc/PID directories) only processes visible in the PID namespace of the process that performed the mount, even if the /proc filesystem is viewed from processes in other namespaces.
The Linux kernel v4.4.0 provides 7 types of namespaces: cgroup, pid, net, mnt, uts, ipc and user.
$ ls -l /proc/$$/ns
total 0
lrwxrwxrwx 1 root root 0 Dec 9 13:08 cgroup -> cgroup:[4026531835]
lrwxrwxrwx 1 root root 0 Dec 9 13:08 ipc -> ipc:[4026531839]
lrwxrwxrwx 1 root root 0 Dec 9 13:08 mnt -> mnt:[4026531840]
lrwxrwxrwx 1 root root 0 Dec 9 13:08 net -> net:[4026531957]
lrwxrwxrwx 1 root root 0 Dec 9 13:08 pid -> pid:[4026531836]
lrwxrwxrwx 1 root root 0 Dec 9 13:08 user -> user:[4026531837]
lrwxrwxrwx 1 root root 0 Dec 9 13:08 uts -> uts:[4026531838]
pid: The Process ID. This file is a handle for the PID namespace of the process.PID namespaces isolate the process ID number space, meaning that processes in different PID namespaces can have the same PID. PID namespaces allow containers to provide functionality such as suspending/resuming the set of processes in the container and migrating the container to a new host while the processes inside the container maintain the same PIDs
If two processes are in the same namespace, then the device IDs and inode numbers of their /proc/[pid]/ns/xxx symbolic links will be the same as shown below cgroup:[4026531835] and other process sharing the same inode.
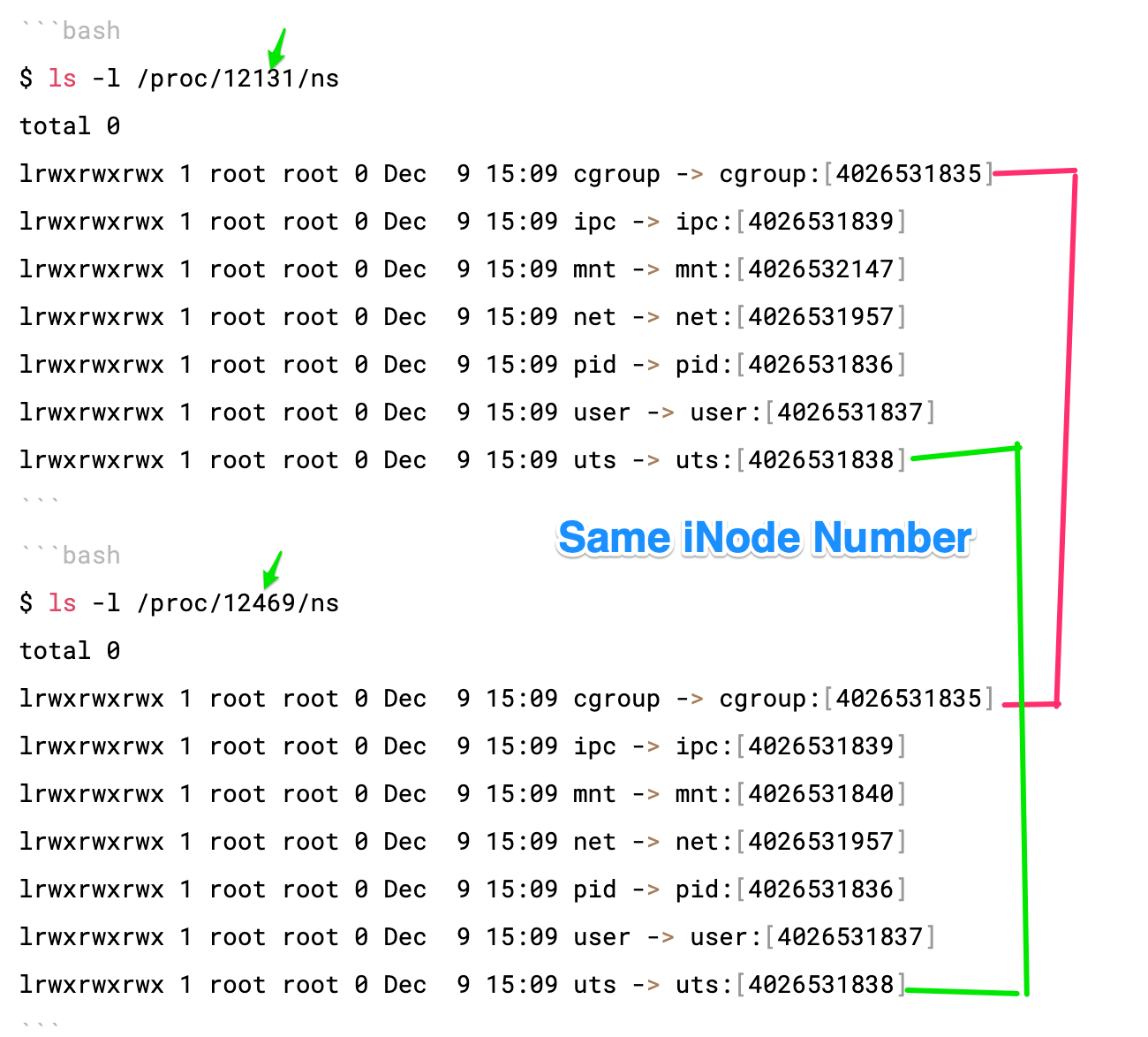
netThis file is a handle for the network namespace of the process. This provides the isolation of the system resources associated with networking and isolates Network devices. Theip netns- is used to process network namespace managementmountThis file is a handle for the mount namespace of the process and isolates Mount pointsipcThis file is a handle for the IPC namespace of the process and isolates System Vs IPC and POSIX message queuesutsThis file is a handle for the UTS namespace of the process and isolates Hostname and NIS domain nameuserThis file is a handle for the user namespace of the processcgroupthe container will have an isolated view of the cgroup hierarchy.
$ cat /proc/cgroups
#subsys_name hierarchy num_cgroups enabled
cpuset 5 3 1
cpu 9 83 1
cpuacct 9 83 1
blkio 10 83 1
memory 8 92 1
devices 2 83 1
freezer 3 3 1
net_cls 4 3 1
perf_event 11 3 1
net_prio 4 3 1
hugetlb 6 3 1
pids
Many container software use Linux namespaces in combination with cgroups to isolate their processes like Docker, LXC, runC.
cgroup vs namespace
- cgroup is a way to control group based traffic control filter, example
"cgroupsPath": "/myRuntime/myContainer",
"resources": {
"memory": {
"limit": 100000,
"reservation": 200000
},
"devices": [
{
"allow": false,
"access": "rwm"
}
]
}
- namespace: Limit/abstraction what you can see in linux proc
Next Reading : How to Monitoring All Executed Commands in Linux
Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Linux Related Topics
Ansible Related Topics
Kubernetes Related Topics
Openstack Articles
Applied Cryptography Topics
Web Crypto API Topics
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile