How To Configure MFA on Centos and Ubuntu with Google Authenticator
by Anish
Posted on Friday October 18/2019

Before We Begin:-
Authentication factor can be of following types: (CISSP Stuff)
- Something you know: A secret or password or PIN
- Something you have: Smart card / token / Mobile Phone
- Something you are: Facial Recognition, Biometrics
Single factor authentication uses one of the types mentioned above as their authentication mechanism for example use of a password to connect to your Linux server
A good example of two-factor authentication is the performing online Transaction, in this case
- Something you know : The Bank user credentials
- Something You have : Phone Number linked with account used to sent OTP for the Two step verification
In this tutorial we will configure our friend SSH to go with MFA, but before that let's take a small chit-chat on TOTP: Time-Based One-Time Password Algorithm
TOTP : The Time-based One-Time Password algorithm (TOTP) is an extension of the HMAC-based One-time Password algorithm (HOTP) generating a one-time password by instead taking uniqueness from the current time.
Google Authenticator is a software-based authenticator that implements two-step verification services using the Time-based One-time Password Algorithm and to achive 2FA in Centos and Ubuntu we will be using google-authenticator-libpam PAM Module.
Let's begin the configuring Google Authenticator PAM Module
- Tested on Ubuntu 16.04/18.04
- Centos7
1. Install google-authenticator
- Ubuntu
sudo apt-get install libpam-google-authenticator
- Centos
yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
yum install google-authenticator
2. Edit the configuration files
-
Edit
/etc/pam.d/sshdand add this directive add it in the beginning of the file. In this way the system will ask first authentication code and only then will ask password.# Google Authenticator auth required pam_google_authenticator.so
-
Edit
/etc/ssh/sshd_configand modify or add these directives:ChallengeResponseAuthentication yes UsePAM yes PasswordAuthentication no
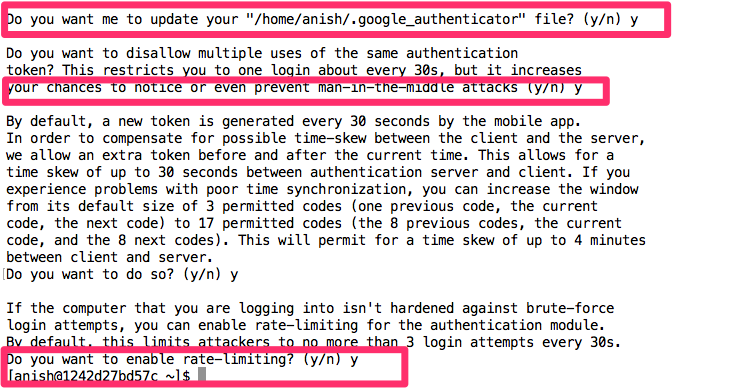
3. Activate the two-factor authentication for a user
Switch to the user who should use the two-factor authentication and type in the terminal:
[anish@1242d27bd57c ~]$ google-authenticator
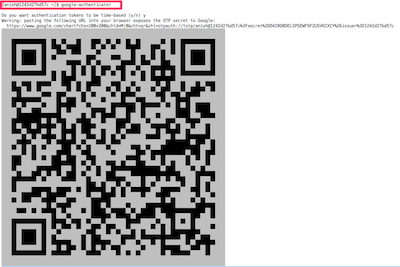
O4IRDBDELSPSEWFXF2USVKIXIY
Your verification code is 560634
Your emergency scratch codes are:
33932408
43900036
59855459
94779765
560436451
you can also find these details in the user home location
anish@1242d27bd57c ~$ cat .google_authenticator
O4IRDBDELSPSEWFXF2USVKIXIY
RATE_LIMIT 3 30
WINDOW_SIZE 17
DISALLOW_REUSE
TOTP_AUTH
33932408
43900036
59855459
94779765
56043645
4. Generate TOTP codes
The Secret Key O4IRDBDELSPSEWFXF2USVKIXIY is used to generate the Authentication code
We will use the Google Authenticator app available for Android (in the Play Store) and iOS (in iTunes) to generate authentication codes.
5. Testing
[root@1242d27bd57c /]# ssh [email protected]
Verification code:
Password:
Last login: Fri Oct 18 08:34:22 2019 from 1242d27bd57c
6. Demo
Centos Video Demo
Ubuntu Video Demo
Next Reading Twenty Step to Harden SSH
Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Linux Related Topics
Ansible Related Topics
Kubernetes Related Topics
Openstack Articles
Applied Cryptography Topics
Web Crypto API Topics
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile