Adding Native IPv6 Support to ECS Instance
by Anish
Posted on Monday July 30, 2018
This document provides an overview of various ways to tunnel IPv6 packets over IPv4 networks in ECS Instances
You can Add an routable IPv6 address in Cloud provider like Alicloud,Linonde,DigitalOcean
Before you Begin
Make Sure you have following prerequisites met on the ECS Side running on any cloud Provider
| Precondition | Check |
|---|---|
| ECS Instance is up and Running | Pass |
| Having sudo privilege account or root account | Pass |
| ECS Instance is assigned with public IP | Pass |
| ECS Instance Security Group Allowing ICMP | Pass |
Tunnel broker:
A service that provides tunneled connectivity to the IPv6 Internet. Using Tunnel Broker an IPv6 access service can enable ECS Instances to access over IPv6 .
Few example of Tunnel brokers Providers
- SixXS - IPv6 Deployment & Tunnel Broker
- tunnelbroker.net - Hurricane Electric Free IPv6 Tunnel Broker
- gogo6 Freenet6: Free and Easy IPv6 Connectivity
Hurricane Electric Tunnel broker
In this example we are using HE, tunnel provider
Format of assigned IPv6 addresses
The prefix length assigned to configured tunnels is 128 bits (/128). Tunnels are assigned from prefix 2001:470::/32
Creating HE Tunnel
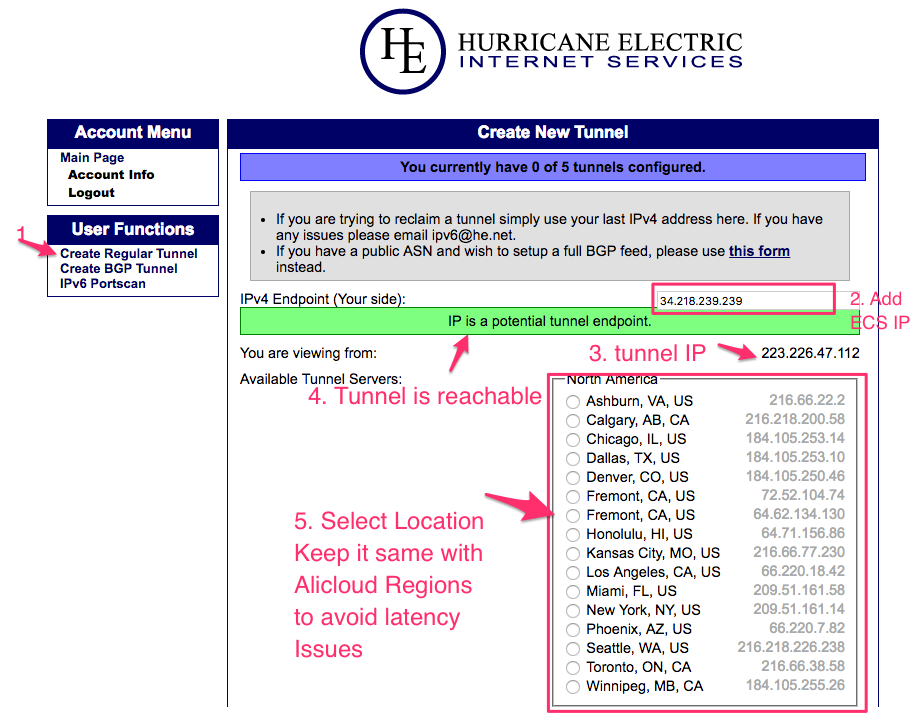
Before creating a Tunnel make sure your ECS instance is up and running and having a routable IPv4 (Ex: 34.218.239.239) assigned
- Create an Account in HE
- Create Regular Tunnel
- When creating new tunnel provide the ECS IP address as show in the diagram
- Select the Location which is very close to Alicloud Region to avoid any Latency Issues
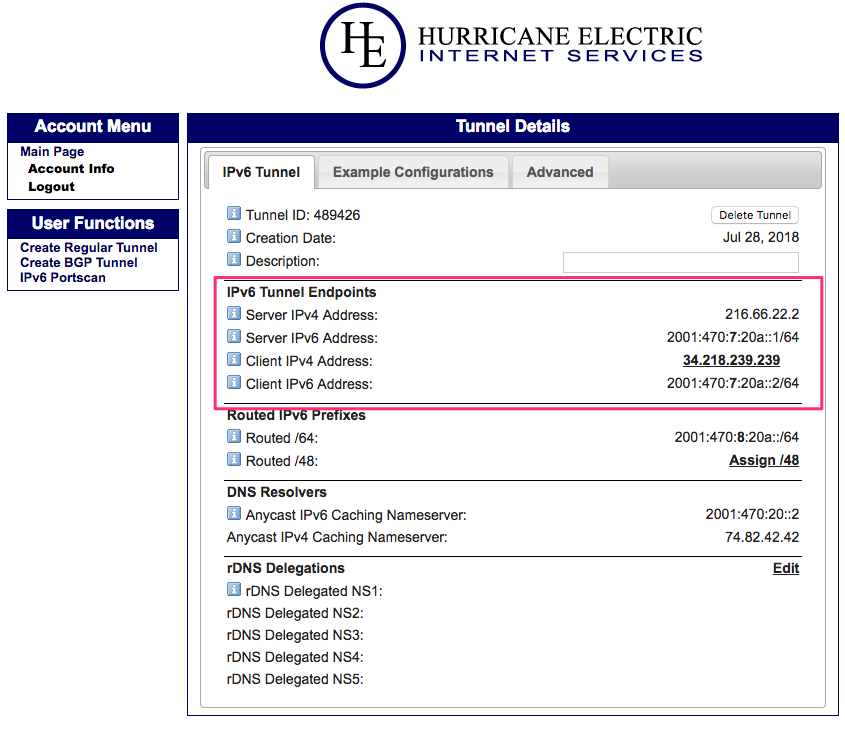
- Once the IPv6 tunnel is created in the HE, you will be displayed with Summary page with tunnel Endpoints note down to the new endpoint configuration

Configure ECS Interface
For EL6
if the ECS instances running on General linux configure * two new interfaces *sit0 for tunnel * and *sit1 for ipv6 address
|tunnel| ipv6 | |--|--| | sit0 | sit1| | ::216.66.22.2 | 2001:470:7:20a::2/64|
Copy and paste the following commands into a command window:
ifconfig sit0 up
ifconfig sit0 inet6 tunnel ::216.66.22.2
ifconfig sit1 up
ifconfig sit1 inet6 add 2001:470:7:20a::2/64
route -A inet6 add ::/0 dev sit1
Check the new interfaces is added sit1 is your IPv6 address which is added to the ECS Instance
[root@ip-172-31-20-124 ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.31.20.124 netmask 255.255.240.0 broadcast 172.31.31.255
inet6 fe80::8e:5fff:fe78:dc2c prefixlen 64 scopeid 0x20<link>
ether 02:8e:5f:78:dc:2c txqueuelen 1000 (Ethernet)
RX packets 11345 bytes 15649422 (14.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1097 bytes 99162 (96.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 8 bytes 648 (648.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 8 bytes 648 (648.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
sit0: flags=193<UP,RUNNING,NOARP> mtu 1480
inet6 ::127.0.0.1 prefixlen 96 scopeid 0x90<compat,host>
inet6 ::172.31.20.124 prefixlen 96 scopeid 0x80<compat,global>
sit txqueuelen 1000 (IPv6-in-IPv4)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
sit1: flags=209<UP,POINTOPOINT,RUNNING,NOARP> mtu 1480
inet6 2001:470:7:20a::2 prefixlen 64 scopeid 0x0<global>
inet6 fe80::ac1f:147c prefixlen 64 scopeid 0x20<link>
sit txqueuelen 1000 (IPv6-in-IPv4)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
For EL7
Copy and paste the following commands into a command window by adjusting with your tunnel configuration
modprobe ipv6
ip tunnel add he-ipv6 mode sit remote 216.66.22.2 local 34.218.239.239 ttl 255
ip link set he-ipv6 up
ip addr add 2001:470:7:20a::2/64 dev he-ipv6
ip route add ::/0 dev he-ipv6
ip -f inet6 addr
For Debian Ubuntu
Paste the following into /etc/network/interfaces: and adjust
auto he-ipv6
iface he-ipv6 inet6 v4tunnel
address 2001:470:7:20a::2
netmask 64
endpoint 216.66.22.2
local 34.218.239.239
ttl 255
gateway 2001:470:7:20a::1
Windows 10
Copy and paste the following commands into a command window:
netsh interface teredo set state disabled
netsh interface ipv6 add v6v4tunnel interface=IP6Tunnel localaddress=34.218.239.239 remoteaddress=216.66.22.2
netsh interface ipv6 add address interface=IP6Tunnel address=2001:470:7:20a::2
netsh interface ipv6 add route prefix=::/0 interface=IP6Tunnel nexthop=2001:470:7:20a::1
Verify the tunnel is working
To verify you need to perform ping6
$ ping6 -c4 2001:470:7:20a::1
PING 2001:470:7:20a::1(2001:470:7:20a::1) 56 data bytes
64 bytes from 2001:470:7:20a::1: icmp_seq=1 ttl=44 time=76.5 ms
64 bytes from 2001:470:7:20a::1: icmp_seq=2 ttl=44 time=76.5 ms
64 bytes from 2001:470:7:20a::1: icmp_seq=3 ttl=44 time=76.5 ms
64 bytes from 2001:470:7:20a::1: icmp_seq=4 ttl=44 time=76.6 ms
--- 2001:470:7:20a::1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 76.515/76.563/76.653/0.343 ms
Alternatively you can use any Online Ipv6 ping the check Ipv6 address

Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Applied Cryptography Topics
Web Crypto API Topics
Linux Related Topics
Ansible Related Topics
Kubernetes Related Topics
Openstack Articles
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile