Light Dive to GPG
by Anish
Posted on Friday July 27, 2018

GPG Celebrating 20 years
GPG the GNU project is a free alternative to PGP, is encryption software that is compliant with the OpenPGP (RFC4880) standard which helps people ensure the confidentiality, integrity and assurance of their data.
For more reference around this project visit GNU
Before you Begin
This sample chapter extracted from the book, The Modern Cryptograhy CookBook . The Book theme isCryptography is for EveryOne. Learn from Crypto Principle to Applied Cryptography With Practical Example
Get this book on Just $9 by availing coupon discount
The example shown in this document will only work on UNIX-based (Linux & OS X) machines,
Little Background
Understanding GPG is complex as many terms used which create confusion, The Idea of this writeup is keep things simple and aligned with the use cases which we deals in our environment.
GPG is fun learning, and once you understand the key concept, you will be amazed !!! how it's differ from TLS.
PGP is based on an introducer-model which depends on the integrity of a chain of authenticators, the users themselves which build a web-of-trust
You might found these terms OpenPGP, PGP, GPG, GPG2 when you google it which is used relatively,
- OpenPGP is Standard is defined in IETF RFC4880
- The GPG software is an independent implementation of the OpenPGP standards
- The GPG2 is a redesigned version of GPG
- PGP : A proprietary encryption solution owned by Symantec.
Key Concept Explained in this Article
What you will going to learn after the end of this Article
- GPG Installation
- Setting up GPG store
- OPenPGP Pem Formats
- GPG Conventions
- GPG Character Code and Descriptions
- GPG Commands
- Listing Keys
- Generating Master keys (Basic Mode)
- Generating Master keys (Expert Mode)
- Export PGP public key from PGP private key
- Import PGP private key
- Encrypting Messages with PGP Public Key
- Decrypting Messages with PGP Public Key
- Delete Keys
- Sign Key
- Create Signature file
- Detach Signature
- Verify Signature
- Editing key Adding UID
- Revoking key
- Create Authenticated Subkey (SSH)
- GnuPG for SSH authentication
GPG Installation
Ubuntu
On Ubuntu, GnuPG 2.0 is available for all supported releases under the package name gnupg2
sudo apt-get install gnupg2
sudo apt-get install gnupg
sudo apt-get install rng-tools
MacOSx
brew install gnupg gpg-agent pinentry-mac
You may have to do:
export GPG_TTY=$(tty)
Linux
yum install gpg
OpenPGP PEM formats
whenever you see message in the below formats, it's considered as PGP Messages, it contains base64 (armor) encoded messages
| OpenPGP Message | Format |
|---|---|
| PGP Public Key |
-----BEGIN PGP PUBLIC KEY BLOCK----- -----END PGP PUBLIC KEY BLOCK----- |
| PGP Private Key |
-----BEGIN PGP PRIVATE KEY BLOCK----- -----END PGP PRIVATE KEY BLOCK------ |
| PGP Message |
----BEGIN PGP MESSAGE----- -----END PGP MESSAGE----- |
Examples
A PGP Public message can be used for encrypting the message
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: BCPG v1.58
mI0EW1iMngEEAJJULdBGqKLBKQcnytCcIU9UbI+awmWn+3mTBEUENhMLIHPo3n+q
brFX/ntOvS/vDK2B1s+haXLbL9HpE+tTRD582tGnoQh4S9qbbSwfMOoh7bx+7Q9M
+SZAPl24Np+c8VqgF5ostDhzS7D9FUS4ziA+mK3tD/8/+9LkP3yE2y0pABEBAAG0
FXphcmlnYXRvbmd5QGdtYWlsLmNvbYicBBABAgAGBQJbWIyeAAoJELRQng4/pli/
kvoD/jczYnysGnv1sLFCkvR1QUHwGrFVG7m8WKY6lz9M+0Zh54OqzsPyZKdE3LMD
jCu7239Pq7L/vaaMbPLao4SePx/AaRi5wgylkvNzl5GtJVQ3PN+t5J9T0CCgSCGy
lp6BWrqz25fRTzkXCPz8Lzt1h3ROaADSPoD8CAmsl8COCciW
=dduA
-----END PGP PUBLIC KEY BLOCK-----
A PGP Private message can be used for decrypting the message
-----BEGIN PGP PRIVATE KEY BLOCK-----
Version: BCPG v1.58
lQH+BFtYjJ4BBACSVC3QRqiiwSkHJ8rQnCFPVGyPmsJlp/t5kwRFBDYTCyBz6N5/
qm6xV/57Tr0v7wytgdbPoWly2y/R6RPrU0Q+fNrRp6EIeEvam20sHzDqIe28fu0P
TPkmQD5duDafnPFaoBeaLLQ4c0uw/RVEuM4gPpit7Q//P/vS5D98hNstKQARAQAB
/gQDAsOHqqoXmSiSYDIcZagYAhFm1aUEa0LTyMDgOGmNrsmFOhYLFpQQbt9De03O
HUVf18pTbztKQ9/E8xM3uy7Afcm/zHpbuTdXeEmD7ukpOefxlicUhnpJpDlcnDFg
140NGY1Nr2V7rvKDU550isUwgwvL/Zgohc4Hfix0y/gNiBIDlYSwmMiRQEsf+c3r
sYtqg+FdYk3q9++PzvwlDPBG56NLOJVHAsjKBEj4XBgftmP+lNw9+MEmzKu/VUPw
UJ7Nqq6E9JSbI+LylOrZ2DF2rI+5KPt1oIlPwckH5u0XNV1tgxl3T4BjCuP9I6S3
S4H5AYTaNeQEGTaOP+88/OuNFd1L5nWTAq79aFV9G2d+7PxOZ6qcP6ETr3BcYZnU
JupsXntbltB1FgxUAzLmlRtJWVwiVTIxYaly3u/wo23TMbPVJi7PiKzmwymCDH2E
Yna4+Z9yXrkk+X8wc+ByLGWGuXRmY8xE2jsfapOyX7NAtBV6YXJpZ2F0b25neUBn
bWFpbC5jb22InAQQAQIABgUCW1iMngAKCRC0UJ4OP6ZYv5L6A/43M2J8rBp79bCx
QpL0dUFB8BqxVRu5vFimOpc/TPtGYeeDqs7D8mSnRNyzA4wru9t/T6uy/72mjGzy
2qOEnj8fwGkYucIMpZLzc5eRrSVUNzzfreSfU9AgoEghspaegVq6s9uX0U85Fwj8
/C87dYd0TmgA0j6A/AgJrJfAjgnIlg==
=BdaL
-----END PGP PRIVATE KEY BLOCK-----
First you need check if there is a gpg key for your ID.
GPG Conventions
There are many codes used in the gpg command output. Familiarize with then
- sec The master/primary secret key. Contains ( key size, keyid, creation date, expiration date and fingerprint)
- ssb Secret Subkeys. These can be your sub signing key, encryption key or authentication key. Users can have multiple subkeys
- uid User information associated with the secret key. You can have multiple uids.
- pub The following is public key Information
- sec#
#after sec means that your secret key is missing from the machine contains a refrence - ssb>
>after ssb means that your subkeys are not the machine. Instead they are on a smartcard (YubiKube) - sub your public subkey info.
GPG Character Code and Descriptions
Few Important flags, which will be output during thegpg --list-keys or gpg --list-secret-keys , lets have a quick summary of thoose
| Flag | Character | Description |
|---|---|---|
| 0x01 | C | Key Certification |
| 0x02 | S | Sign Data |
| 0x04 | E | Encrypted Communication |
| 0x20 | A | Authentication |
Setting up GPG store
The directory ~/.gnupg is where configuration files for GnuPG, the GNU Privacy Guard, reside
setting up ~/.gnupg : This can be done by issues and gpg command
$ gpg --list-keys
gpg: /Users/anish/.gnupg/trustdb.gpg: trustdb created
gpg command
$ gpg -h
GPG List Keys
Well this command server two purpose, if you are running it for the first time, it will create a db for you in your home folder location ~/.gnupg/ where all the keys,certificate will be stored
if the directory ~/.gnupg/ exists, it will fetch the all the public keys only
$ gpg --list-key
/Users/anish/.gnupg/pubring.kbx
pub rsa1024 2018-07-25 [SCEA]
B9DC677415D74D9FEA948D8BB4509E0E3FA658BF
uid [ unknown] [email protected]
Run gpg --list-keys 'your uid' to list the keys associated with the given uid
vm2-$ gpg --list-keys 'anish'
pub rsa2048 2018-07-25 [SC] [expires: 2020-07-24]
8120745E3C9D01A498850EC3548E99438838675A
uid [ultimate] Anish <[email protected]>
sub rsa2048 2018-07-25 [E] [expires: 2020-07-24]
Ok what about my private keys where it's stored
vm2-$ gpg --list-secret-keys
Use the gpg --list-secret-keys --keyid-format LONG command to list GPG keys for which you have both a public and private key.
vm2-$ gpg --list-secret-keys --keyid-format LONG
Generating Master keys (Basic Mode)
Generate a new key pair with default option will not give you capabilities option to further secure your keys (Like Expiry/Cipher Algo preference)
vm2-$ gpg --gen-key
........ ...... ...... ......
Real name: Anish
Email address: [email protected]
You selected this USER-ID:
"Anish <[email protected]>"
Image gpg3/4
Change (N)ame, (E)mail, or (O)kay/(Q)uit? O
...... ...... ...... ...... ......
gpg: key 548E99438838675A marked as ultimately trusted
gpg: directory '/Users/anish/.gnupg/openpgp-revocs.d' created
gpg: revocation certificate stored as '/Users/anish/.gnupg/openpgp-revocs.d/8120745E3C9D01A498850EC3548E99438838675A.rev'
public and secret key created and signed.
pub rsa2048 2018-07-25 [SC] [expires: 2020-07-24]
8120745E3C9D01A498850EC3548E99438838675A
uid Anish <[email protected]>
sub rsa2048 2018-07-25 [E] [expires: 2020-07-24]
Invoke gpg --full-generate-key to expose some additional menu items.
Generating Master keys (Expert Mode)
Invoke gpg --gen-key with the --expert flag to expose some additional menu items.
- MacOSX
vm2-$ gpg --full-generate-key - Linux
vm2-$ gpg --expert --gen-key
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
Choose the Algorithm from the given option (RSA/DSA/Elgamal)
Your selection? 4RSA keys may be between 1024 and 4096 bits long. What keysize do you want? (2048) Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Specifying the Key Expiry Data, Based on the type of Key Harden your Expiry requirement here
Key is valid for? (0) 3y
Key expires at Sat Jul 24 21:06:35 2021 IST
Is this correct? (y/N)
GnuPG needs to construct a user ID to identify your key.
Associate Identity to this key
Real name: anishn Email address: [email protected] Comment: MySecureKeyChange (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
List out your Public Keys
vm2-$ gpg --list-keys
/root/.gnupg/pubring.gpg
------------------------
pub 2048R/9605D032 2018-07-26 [expires: 2021-07-25]
uid anishn (MySecureKey) <[email protected]>
List out your Private Keys
vm2-$ gpg --list-secret-keys
/root/.gnupg/secring.gpg
------------------------
sec 2048R/9605D032 2018-07-26 [expires: 2021-07-25]
uid anishn (MySecureKey) <[email protected]>
Encrypting Messages with PGP Public Key
Use the gpg --armor --encrypt --recipient <uid> command to encrypt the message. The --armor option will output the encrypted message in base64 encoded
Text Encyption
vm2-$ echo "Hello 8gwifi.org" | gpg --armor --encrypt --recipient [email protected] > pgpencypted.txt
gpg: B4509E0E3FA658BF: There is no assurance this key belongs to the named user
pub rsa1024/B4509E0E3FA658BF 2018-07-25 [email protected]
Primary key fingerprint: B9DC 6774 15D7 4D9F EA94 8D8B B450 9E0E 3FA6 58BF
The armor output PGP Message
vm2-$ cat pgpencypted.txt
-----BEGIN PGP MESSAGE-----
hIwDtFCeDj+mWL8BA/9S2AZauDug0lzHl6Qc2qkqhKQ+dVUZ9xdi3leUA36Pr9BH
v9JmccnJbQCc69mth3a/paK4nVYy/APoI+5n5X4HU+K3Vl47aGAxj4R2oitR5V5Z
zUvJb7pOR2SZ9tEq/995ZTqzVVy8pmLzKFZklUj7JxALH3Hs533hQAfIx6htLtI+
AXJ+L3vwHM1N6XjjSjGJAFw3diQtNyeCHwLGU+u6DHFf3AS234PPE3Vj2tr1bjSo
zB5XDTtHXiLpkwZQdOI=
=7d1u
-----END PGP MESSAGE-----
File Encryption
gpg -r [email protected] --encrypt file-to-encrypt
Decrypting Messages with PGP Public Key
Use the gpg --output decrypted.txt --no-tty <filename> command to decrypt the message.
vm2-$ gpg --output decrypted.txt --no-tty pgpencypted.txt

gpg: WARNING: no command supplied. Trying to guess what you mean ...
gpg: encrypted with 2048-bit RSA key, ID 1AFA5B35FAA8D03B, created 2018-07-25
"Anish zarigatongy@gmail.com"Verify the output of the file
vm2-$ cat decrypted.txt
Hello 8gwifi
Import private key
Use the `gpg --import <filename> ` command to import your pgp private key
vm2-$ gpg --import privkey.pem
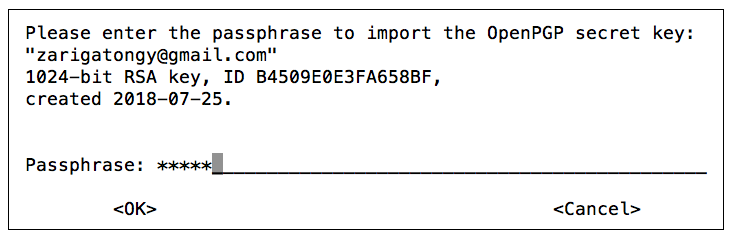
gpg: key B4509E0E3FA658BF: public key "[email protected]" imported
gpg: key B4509E0E3FA658BF: secret key imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
Export PGP public key from PGP private key
use the gpg --export <fingerprint> or gpg --export <uid> option to export public key
This will Export in Binary format
vm2-$ gpg --export 8120745E3C9D01A498850EC3548E99438838675A > pub.gpg
ASCII-armoured public key.
vm2-$ gpg -a --export 8120745E3C9D01A498850EC3548E99438838675A > pub.asc
or
gpg -a --export anishn > pub.asc
vm2-$ cat pub.asc
The PGP Public Key file
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBFtYkZwBCACk/0K0e4V46ZOk42Roa+HvZNTY7u76yrvN0YyuI8ZR0h/m7u/H
4bIk9R/e7PgbnP+MjSJGcZMa+Eq6bk1848mS7rZXdeF7TZN3oc1efKg6oOFQKcpB
........
........
-----END PGP PUBLIC KEY BLOCK-----
Now using this PGP Public key Message can be encrypted
Use Export Option to Backup PGP keys
generate base64-encoded armored backups
gpg --armor --export > pgp-public-keys.asc
gpg --armor --export-secret-keys > pgp-private-keys.asc
gpg --export-ownertrust > pgp-ownertrust.asc
To restore it
gpg --import pgp-public-keys.asc
gpg --import pgp-private-keys.asc
gpg --import-ownertrust pgp-ownertrust.ascUpload the key to the key server network
Usually, keys are distributed using the key server network. Uploading your public key is very easy using the --send-key command.
gpg --send-key [key-id]
Search and receive your key by executing
Search and receive your key by executing
gpg --search [mail address]
gpg --recv-key [key-id]
Edit Keys
you can edit your existing keys to perform many function offered by GPG, use the gpg --edit-key <id> command
gpg --edit-key D3CEAB0F
Few example of performing --edit-key operation
Adding Another UID
In this example we are associating an email with your GPG key id name D3CEAB0Fgpg> adduid
Real name: anish2
Email address: [email protected]
Comment: mysecondkey
You selected this USER-ID:
"anish2 (mysecondkey) <[email protected]>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
At the end you will see another key is added not the trust level is set to unknown here key2
pub 2048R/D3CEAB0F created: 2018-07-26 expires: 2021-07-25 usage: SC trust: ultimate validity: ultimate [ultimate] (1) anishn (My Trustedkey) <[email protected]> [ unknown] (2). anish2 (mysecondkey) <[email protected]>Finally Save the configuration
gpg> save
List key will show newly added key with the new Identity associated with your public key
vm2-$ gpg --list-key
/root/.gnupg/pubring.gpg
------------------------
pub 2048R/D3CEAB0F 2018-07-26 [expires: 2021-07-25]
uid anish2 (mysecondkey) <[email protected]>
uid anishn (My Trustedkey) <[email protected]>
Changing Trust Level
change the trust level of your key by using the command gpg --edit-key <key-id> trust
Decide the trust level
1 = I don't know or won't say
2 = I do NOT trust
3 = I trust marginally
4 = I trust fully
5 = I trust ultimately
m = back to the main menu
Revoking the key
vm2-$ gpg --edit-key anishn
pub 2048R/A31E5C75 created: 2018-07-26 expires: 2021-07-25 usage: SC
trust: ultimate validity: ultimate
sub 2048R/20EE3BF8 created: 2018-07-26 expires: 2021-07-25 usage: A
[ultimate] (1). anishn (MySecure Key) <[email protected]>
Select Which key need to revoked,
gpg> key 1
pub 2048R/A31E5C75 created: 2018-07-26 expires: 2021-07-25 usage: SC
trust: ultimate validity: ultimate
sub* 2048R/20EE3BF8 created: 2018-07-26 expires: 2021-07-25 usage: A
[ultimate] (1). anishn (MySecure Key) <[email protected]>
Issue the revkey command
gpg> revkey
Do you really want to revoke this subkey? (y/N) y
Please select the reason for the revocation:
0 = No reason specified
1 = Key has been compromised
2 = Key is superseded
3 = Key is no longer used
Q = Cancel
Your decision? 0
Enter an optional description; end it with an empty line:
>
Reason for revocation: No reason specified
(No description given)
Is this okay? (y/N) y
It requires passphrase of unlocking , Provide the password
You need a passphrase to unlock the secret key for
user: "anishn (MySecure Key) <[email protected]>"
2048-bit RSA key, ID A31E5C75, created 2018-07-26
pub 2048R/A31E5C75 created: 2018-07-26 expires: 2021-07-25 usage: SC
trust: ultimate validity: ultimate
This key was revoked on 2018-07-26 by RSA key A31E5C75 anishn (MySecure Key) <[email protected]>
sub 2048R/20EE3BF8 created: 2018-07-26 revoked: 2018-07-26 usage: A
[ultimate] (1). anishn (MySecure Key) <[email protected]>
gpg> save
Delete Keys
use option gpg --delete-secret-keys to delete the secret key first
use the gpg --delete-key <fingerprint> or gpg --delete-key <uid> to delete the key
vm2-$ gpg --delete-secret-keys [email protected]
It will prompt for confirmation
 Then delete the key
vm2-$ gpg --delete-key [email protected]
Then delete the key
vm2-$ gpg --delete-key [email protected]
Singing user key
When you sign the key, it means you verify that you trust the person is who they claim to be
use option gpg --sign-key <uid> to sign the user key
vm2-$ gpg --sign-key [email protected]
pub rsa1024/B4509E0E3FA658BF
created: 2018-07-25 expires: never usage: SCEA
trust: unknown validity: unknown
[ unknown] (1). [email protected]
pub rsa1024/B4509E0E3FA658BF
created: 2018-07-25 expires: never usage: SCEA
trust: unknown validity: unknown
Primary key fingerprint: B9DC 6774 15D7 4D9F EA94 8D8B B450 9E0E 3FA6 58BF
[email protected]
Are you sure that you want to sign this key with your
key "Anish <[email protected]>" (548E99438838675A)
Image gpg6
Really sign? (y/N) y
vm2-$ gpg --output signed.key --export --armor [email protected]
Creating Signature for file
To create Signature of any given file, this will use default-key
gpg --output out.sig --sign filename
To create signature with different key add --local-user <uid> option
gpg --local-user test3 --output out.sig --sign filename
You need a passphrase to unlock the secret key for
user: "test3"
1024-bit RSA key, ID 57ED5CD6, created 2018-07-26
The document is compressed before signed, and the output is in binary format.
Detached Signature
A detached signature is created using the --detach-sig option.
To detach signature not signed by default key pass the --local-user
gpg --local-user test3 --output out.sig --detach-sig filename
With default key gpg --output out.sig --detach-sig filename
Verifying Signature
After detaching the signature ato verify the signature. The --verify option can be to check the signature.
gpg --verify out.sig doc
gpg: Signature made Thu 26 Jul 2018 11:18:33 AM EDT using RSA key ID D3CEAB0F
gpg: Good signature from "anish2 (mysecondkey) <[email protected]>"
gpg: aka "anishn (My Trustedkey) <[email protected]>"
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 88C4 A883 500D D788 2B0C 7082 372B B5E9 D3CE AB0F
Create Authenticate key (SSH)
In this example we will add a new key that will be used for SSH Authentication
Edit your OpenPGP key such as the following:
vm2-$ gpg --expert --edit-key anishn
gpg> addkey Key is protected.
You need a passphrase to unlock the secret key for Once password is verified it will prompt for the menu
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
Select (8) RSA (set your own capabilities):
Your selection? 8
Select successively (S), (E), and (A) to remove the signing and encryption capabilities and enable the authentication capability. Possible actions for a RSA key: Sign Encrypt Authenticate Current allowed actions: Sign Encrypt
**(S) Toggle the sign capability**
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
**Your selection? S**
Select E on the Next Prompt
(S) Toggle the sign capability
**(E) Toggle the encrypt capability**
(A) Toggle the authenticate capability
(Q) Finished
**Your selection? E**
select A (Toggle the authenticate capability)
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions:
(S) Toggle the sign capability
(E) Toggle the encrypt capability
**(A) Toggle the authenticate capability**
(Q) Finished
**Your selection? A**
Finally Finished by Selecting Q
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Authenticate
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
**(Q) Finished**
select (Q) Finished to exit this sub-menu. The remaining of the procedure is like any other key generation:
**Your selection? Q**
Configure RSA Keys (2048 Bits )
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Setup Expiry
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
**Key is valid for? (0) 1y**
Key expires at Thu Jul 25 21:23:31 2019 IST
Is this correct? (y/N) y
Really create? (y/N) y
........
At the end Notice the usgae is set to A
pub 2048R/D3CEAB0F created: 2018-07-26 expires: 2021-07-25 usage: SC
trust: full validity: unknown
sub 2048R/6445A49E created: 2018-07-26 expires: 2019-07-26 **usage: A**
[ unknown] (1). anish2 (mysecondkey) <[email protected]>
[ unknown] (2) anishn (My Trustedkey) <[email protected]>
gpg> quit
Save changes? (y/N) y
Export Subkey
Export your subkey by replacing key-id with the eight-character key ID :
vm2-$ gpg -a --export-secret-subkeys 20EE3BF8 >> mysub.key
Sample Output
vm2-$ cat mysub.key
-----BEGIN PGP PRIVATE KEY BLOCK-----
......................
lQM2BFtYmZwRCACB+Umh4N1LSpWzm4sDHI0dhiykpdPWIQ9ADMMJD/NxsTMQvCfO
......................
......................
-----END PGP PRIVATE KEY BLOCK-----
GnuPG for SSH authentication
To use PGP keys as authentication keys, first create the Authentication key, which is explained earlier
Install necessary Packages , monkeysphere provides openpgp2ssh
apt-get install monkeysphere
apt-get install rng-tools
apt-get install gnupg-agent
- Start gpg-agent
eval $( gpg-agent --daemon --disable-scdaemon --enable-ssh-support ) - Verify Agent is running
vm2-$ eval `ssh-agent -s`
Agent pid 13138
- Export the Authentication key
vm2-$ gpg --export-options export-reset-subkey-passwd,export-minimal,no-export-attributes --export-secret-subkeys 20EE3BF8 | openpgp2ssh 20EE3BF8 > '.anishn'
- Add this key in
~/.gnupg/private-keys-v1.d/
vm2-$ ssh-add '.anishn'
Identity added: .anishn (.anishn)
This will store a copy of the key in ~/.gnupg/private-keys-v1.d/. It will also add the keygrp of the subkey to ~/.gnupg/sshcontrol.
- Verify
vm2-$ ls -l ~/.gnupg/private-keys-v1.d/
total 4
-rw-r----- 1 root root 1194 Jul 26 00:21 40B0A8A78B1E9153848E820D80573E3906B1A390.key
- Serve Your GPG key Instead of an SSH key To check that it has worked you can do ssh-add -l
vm2-$ ssh-add -l
2048 02:b2:c5:0f:e9:3a:66:fe:79:5d:4f:07:e7:dc:5a:8a .anishn (RSA)
vm2-$ ssh-add -L
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDb7PMpbTnh1UF3RpcKZBPwIf0NhkFc8uD5U1w9yrD0FtyT20c2H+EsZxJtb1cu/huQ/UG1opVWtucCvH/6sF2F+K2mnUmUIlqS+zlZAKJKd6Jf0Zo7hSgKCgYkiUevuTr5GFVxDQw5PTHYHjay2NXHvUF/mp7A9XfqeuK8MX9iL1nh+sp2vAF7dtNGpn3IRGwEZFYFO0arUIsiqEvazm1sWEQKRxQl/KHn8O0TisGJLvh2T48rDIJ5HEO1Lax6ZULnWPFnsMP84jLW1tA4eBkZ+CPqYnua5Y/rXjYjaW1XrBI7GAtmJ5FHsv4TMKGN3cwTc83HVag0TFL1qmdOkov9 .anishn
- Save this Key to a file
ssh-add -L >> authorized_keys - copy this authorized key to the remote machine
vm2-$ scp authorized_keys [email protected]:~/.ssh/
[email protected]'s password:
authorized_keys 100% 776 0.8KB/s 00:00
- Verify the Login
vm2-$ ssh [email protected]
Welcome to Ubuntu 14.04.1 LTS (GNU/Linux 3.13.0-32-generic x86_64)
start gpg-agent automatically, Edit the ~/.bash_profile
if [ -f "${HOME}/.gpg-agent-info" ]; then source "${HOME}/.gpg-agent-info" export GPGAGENTINFO export SSHAUTHSOCK export SSHAGENTPID else eval $( gpg-agent --daemon --write-env-file ~/.gpg-agent-info ) fi
Create ~/.gnupg/gpg-agent.conf
default-cache-ttl 3600 max-cache-ttl 7200 enable-ssh-support write-env-file ~/.gpg-agent-info
Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Applied Cryptography Topics
Web Crypto API Topics
Linux Related Topics
Ansible Related Topics
Kubernetes Related Topics
Openstack Articles
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile