Letsencrypt Obtain Wild Card Certificate Using DNS challenge and Kubernetes
by Anish
Posted on Wednesday August 21, 2019

Introduction
In this exercise we will learn how to obtain Letsencrypt wild card certificate for your domain using DNS-01 challenge for this example i have used the domain name 0cloud0.com and then uses the certificate and key and add it into the kubernetes cluster
The CN entry is going to look like this : CN=0cloud0.com and CN=*.0cloud0.com
When you get a certificate from Let's Encrypt, they validate that you control the domain names in that certificate using challenges as defined by the ACME standard.
Let's Encrypt supports two methods of validation to prove control of your domain, http-01 validation over HTTP and dns-01 (validation over DNS).
In order to validate your control of your domains to the certificate authority you will be required to create a specified TXT record in your domain's DNS zone.
Many DNS provider offer these TXT record to be created using their API keys as an solution.
About LEGO
Let's Encrypt client and ACME library written in Go which gives you robost implementation of all ACME challenges. In this example we are going to use CLOUDFLARE as and DNS provider and request this provider to issues the certificates.
First download the lego binary installer from lego release github
Since we are working with CLOUDFLARE DNS, to access the obtain the CLOUDFLARE API KEY
- Setup the Necessary Request Header
bash ~ export CLOUDFLARE_API_KEY=YOUR_KEY
bash ~ export [email protected]
- Use lego to Issues a DNS-01 challenge and wait for command to complete
>bash ~ ./lego --dns cloudflare --domains 0cloud0.com --domains *.0cloud0.com --email [email protected] run
The command output
2019/08/20 08:03:35 [INFO] [0cloud0.com, *.0cloud0.com] acme: Obtaining bundled SAN certificate
2019/08/20 08:03:37 [INFO] [*.0cloud0.com] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz/wblN31seRjbNLtmBVY7rVsRskS05Ns5Mqn-XJYwY8vY
2019/08/20 08:03:37 [INFO] [0cloud0.com] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz/BwcA9yFqo6z_OErtyL3fzWEv3Jfu-CcZuEPTUDE3lvg
2019/08/20 08:03:37 [INFO] [*.0cloud0.com] acme: use dns-01 solver
2019/08/20 08:03:37 [INFO] [0cloud0.com] acme: Could not find solver for: tls-alpn-01
2019/08/20 08:03:37 [INFO] [0cloud0.com] acme: Could not find solver for: http-01
2019/08/20 08:03:37 [INFO] [0cloud0.com] acme: use dns-01 solver
2019/08/20 08:03:37 [INFO] [*.0cloud0.com] acme: Preparing to solve DNS-01
2019/08/20 08:03:39 [INFO] cloudflare: new record for 0cloud0.com, ID af899d5fdd66b7e36cbe0c30f55deeea
2019/08/20 08:03:39 [INFO] [0cloud0.com] acme: Preparing to solve DNS-01
2019/08/20 08:03:40 [INFO] cloudflare: new record for 0cloud0.com, ID 262d43cbfa3df100e35dc3527e23d1e7
2019/08/20 08:03:40 [INFO] [*.0cloud0.com] acme: Trying to solve DNS-01
2019/08/20 08:03:40 [INFO] [*.0cloud0.com] acme: Checking DNS record propagation using [192.168.1.1:53]
2019/08/20 08:03:40 [INFO] Wait for propagation [timeout: 2m0s, interval: 2s]
2019/08/20 08:03:41 [INFO] [*.0cloud0.com] acme: Waiting for DNS record propagation.
2019/08/20 08:03:45 [INFO] [*.0cloud0.com] The server validated our request
2019/08/20 08:03:45 [INFO] [0cloud0.com] acme: Trying to solve DNS-01
2019/08/20 08:03:45 [INFO] [0cloud0.com] acme: Checking DNS record propagation using [192.168.1.1:53]
2019/08/20 08:03:45 [INFO] Wait for propagation [timeout: 2m0s, interval: 2s]
2019/08/20 08:04:40 [INFO] [0cloud0.com] The server validated our request
2019/08/20 08:04:40 [INFO] [*.0cloud0.com] acme: Cleaning DNS-01 challenge
2019/08/20 08:04:42 [INFO] [0cloud0.com] acme: Cleaning DNS-01 challenge
2019/08/20 08:04:42 [INFO] [0cloud0.com, *.0cloud0.com] acme: Validations succeeded; requesting certificates
2019/08/20 08:04:44 [INFO] [0cloud0.com] Server responded with a certificate.
- Once the validation is succeeded your certificate and key file will get stored in the
$ ls .lego/*
.lego/accounts:
acme-v02.api.letsencrypt.org
.lego/certificates:
0cloud0.com.crt 0cloud0.com.issuer.crt 0cloud0.com.json 0cloud0.com.key
- From here you can create kubernetes secrets and add your tls key and cert file
root@kube-master:~# kubectl create secret tls 0cloud0-wildcard-certs --key 0cloud0.com.key --cert 0cloud0.com.crt
secret/0cloud0-wildcard-certs created
- Describe the secrets
root@kube-master:~# kubectl describe secrets 0cloud0-wildcard-certs
Name: 0cloud0-wildcard-certs
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/tls
Data
====
tls.key: 288 bytes
tls.crt: 3332 bytes
- You can create an Ingress file to deploy the certificate for your domain 0cloud0.com
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: zeroclouddeploy
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/force-ssl-redirect: 'true'
ingress.kubernetes.io/ssl-redirect: "true"
spec:
rules:
- host: 0cloud0.com
http:
paths:
- path: /
backend:
serviceName: zerocloud
servicePort: 8080
tls:
- secretName: 0cloud0-wildcard-certs
hosts:
- 0cloud0.com
root@kube-master:~# kubectl apply -f ingress.yml
ingress.extensions/zeroclouddeploy configured
- Verify the domain https://0cloud0.com
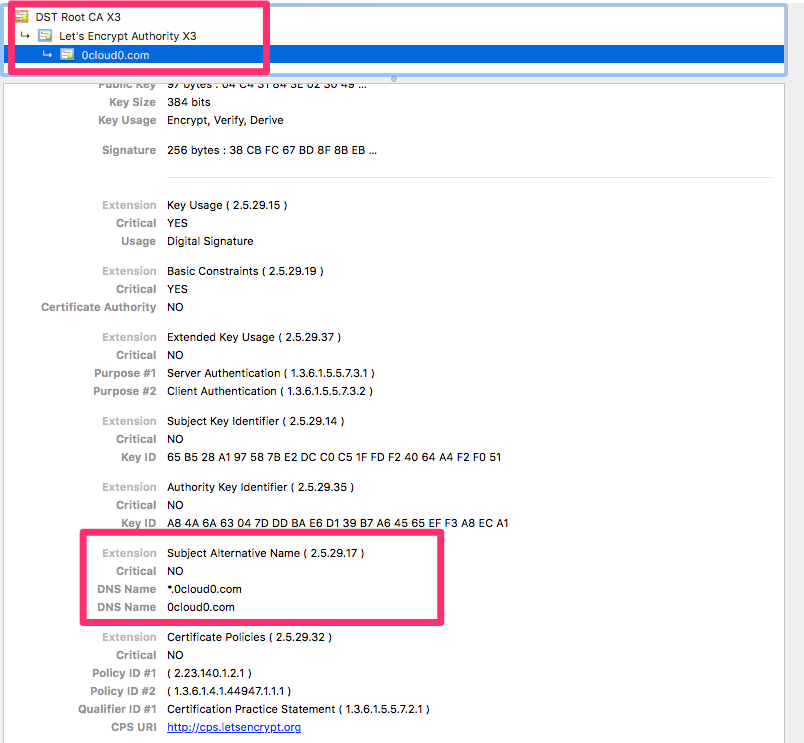
Using Cert-manager
In the previous example we have learn how to obtain certificate using HTTP-01 challenge, In this example we will use cert manager to configure DNS-01 challenge to obtain wildcard Certificate for your given domain name
DNS Provider Cloudflare
- First Configure the Issuer replace and the email, this example uses production certificate
apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
server: https://acme-v02.api.letsencrypt.org/directory
email: 'EMAIL'
privateKeySecretRef:
name: letsencrypt-prod
# http01: {}
dns01:
providers:
- name: cf-dns
cloudflare:
email: 'EMAIL'
apiKeySecretRef:
name: cloudflare-api-key
key: api-key
- Create Secrets
API_KEY=$(echo MY_CLOUDFLARE_KEY | base64 -)
cat <<EOF | kubectl apply -f -
---
apiVersion: v1
kind: Secret
metadata:
name: cloudflare-api-key
type: Opaque
data:
api-key: $API_KEY
EOF
- Issue certificate
apiVersion: certmanager.k8s.io/v1alpha1
kind: Certificate
metadata:
name: 0cloud0wildcard
spec:
secretName: 0cloud0-wild-certs1
issuerRef:
name: letsencrypt-prod
kind: ClusterIssuer
commonName: '*.0cloud0.com'
acme:
config:
- dns01:
provider: cf-dns
domains:
- '*.0cloud0.com'
DNS Provider AWS Route53
To configure AWS the following is needed
- AWS_ACCESS_KEY_ID
- AWS_HOSTED_ZONE_ID
- AWS_REGION
- AWS_SECRET_ACCESS_KEY
This is the YAML definition for configuring the cert-manager to Issue letsencrypt staging certificate
---
apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: route53Issuer
spec:
acme:
email: YOUR_EMAIL
server: https://acme-staging-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt-staging
dns01:
providers:
- name: route53
route53:
region: us-east-1
accessKeyID: AKIABCDEFGHIJKLMNOPQ
secretAccessKeySecretRef:
name: aws-apikey
key: SecretAccessKey
---
apiVersion: v1
kind: Secret
metadata:
name: aws-apikey
type: Opaque
data:
SecretAccessKey: YmxhaGJsYWhibGFoYmxhaGJsYWhibGFo
Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Kubernetes Related Topics
Linux Related Topics
Ansible Related Topics
Openstack Articles
Applied Cryptography Topics
Web Crypto API Topics
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile