Kubernetes Ingress (Traefik)
by Anish
Posted on Wednesday January 23, 2019
Introduction
Kubernetes is the great way to manage docker service in the orchestration way, the service which are created need to be exposed to external clients, which can be done in many ways, This tutorial explains how to use Traefik as an Ingress controller for a Kubernetes cluster
Exposing services to external clients
In kubernetes these are the defined way to make service accessible externally we better known as
- Node port : Exposes the service on each Node's IP at a static port (the
NodePort) - Loadbalancer; Exposes the service externally using a cloud provider's load balancer.
NodePortandClusterIPservices, to which the external load balancer will route, are automatically created. - Ingress Resource : This operates on the at the application layer7, in TCP/IP stack, the HTTP level and offer more feature than layer4 service.
This tutorial is dedicated to use Ingress Resource using the Traefik Kubernetes Ingress Controller
if you have not setup the traefik yet in k8 cluster then, Click here to Setup Traefik in k8 cluster
About Traefik
Traefik is a modern HTTP reverse proxy and load balancer that makes deploying microservices easy. Traefik integrates with your existing infrastructure components and configures itself automatically and dynamically. Pointing Traefik at your orchestrator should be the only configuration step you need.
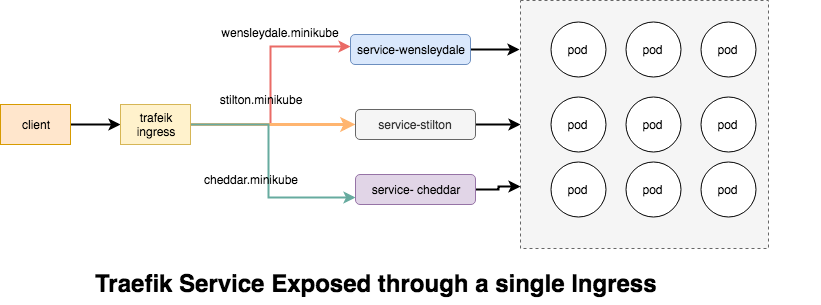
Traefik Ingresses operate at the application layer of the network stack (HTTP) and can provide features such as cookie-based session affinity and the like, which services can't.
The Example Application
We are going here to setup three sample nginx cheese web application, the docker images are located here .
- Docker image: errm/cheese:wensleydale
- Docker image: errm/cheese:cheddar
- Docker image: errm/cheese:stilton
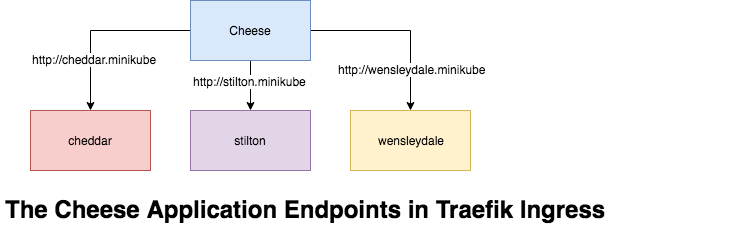
What is Name based routing ?
The Name-Based Routing performs routing by name and support routing HTTP traffic to multiple host names at the same IP address but different domain names , lets start by launching the pods for the cheese websites.
Deployment of Cheese Web Application
root@kube-master:# kubectl apply -f https://raw.githubusercontent.com/containous/traefik/master/examples/k8s/cheese-deployments.yaml
deployment.extensions/stilton created
deployment.extensions/cheddar created
deployment.extensions/wensleydale created
To provide some explanations about the file content:
- We define a deployment (
kind: Deployment) - The name of the object is "stilton" (
name: stilton) - We want one replica (
replicas: 2) - It will deploy pods that have the label app:cheese (
selector: matchLabels: app:cheese) - Then we define the pods (
template: ...) - The Pods will have the cheese label (
metadata:labels:app:cheese) - The Pods will host a container using the image tag errm/cheese:stilton (
image: errm/cheese:stilton) - The same deployment is repeated for cheddar and wensleydale
Make sure all the deployment pods are up and running
root@kube-master:/home/ansible# kubectl get pods
NAME READY STATUS RESTARTS AGE
cheddar-6c895c7cc7-2qztp 1/1 Running 0 7m
cheddar-6c895c7cc7-mzq9v 1/1 Running 0 7m
stilton-7989d7c86f-62wrt 1/1 Running 0 7m
stilton-7989d7c86f-fjttz 1/1 Running 0 7m
wensleydale-58784fc6f7-f8szd 1/1 Running 0 7m
wensleydale-58784fc6f7-prb8z 1/1 Running 0 7m
Service Cheese Web Application
Next we need to setup a Service for each of the cheese pods.
root@kube-master:# kubectl apply -f https://raw.githubusercontent.com/containous/traefik/master/examples/k8s/cheese-services.yaml
service/stilton created
service/cheddar created
service/wensleydale created
All the
root@kube-master:/home/ansible# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
cheddar ClusterIP 10.108.200.238 <none> 80/TCP 30s
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 1h
stilton ClusterIP 10.102.20.8 <none> 80/TCP 30s
wensleydale ClusterIP 10.109.58.21 <none> 80/TCP 30s
At this point, we have deployment and Service ready in the K8 cluster, and we're about to define the ingress rules so that the world can eat the required service.
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: cheese
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: stilton.minikube
http:
paths:
- path: /
backend:
serviceName: stilton
servicePort: http
- host: cheddar.minikube
http:
paths:
- path: /
backend:
serviceName: cheddar
servicePort: http
- host: wensleydale.minikube
http:
paths:
- path: /
backend:
serviceName: wensleydale
servicePort: http
To provide some explanations about the file content:
- We define a Ingress (
kind: Ingress) - The name of the object is "cheese" (
name: cheese) - Then we define the rules (
rules: ...) - For each service there is hostname defined for example the hostname stilton.minikube is mapped to stilton service.
- The rules are repeated for each service.
- Let's apply this rule in k8 cluster
root@kube-master:/home/ansible# kubectl apply -f https://raw.githubusercontent.com/containous/traefik/master/examples/k8s/cheese-ingress.yaml
ingress.extensions/cheese created
Verify the Ingress, all the hosts can be accessed with the ingress port 80
root@kube-master:/home/ansible# kubectl get ingress
NAME HOSTS ADDRESS PORTS AGE
cheese stilton.minikube,cheddar.minikube,wensleydale.minikube 80 31s
Now visit the Traefik dashboard and you should see a frontend for each host. Along with a backend listing for each service with a server set up for each pod.
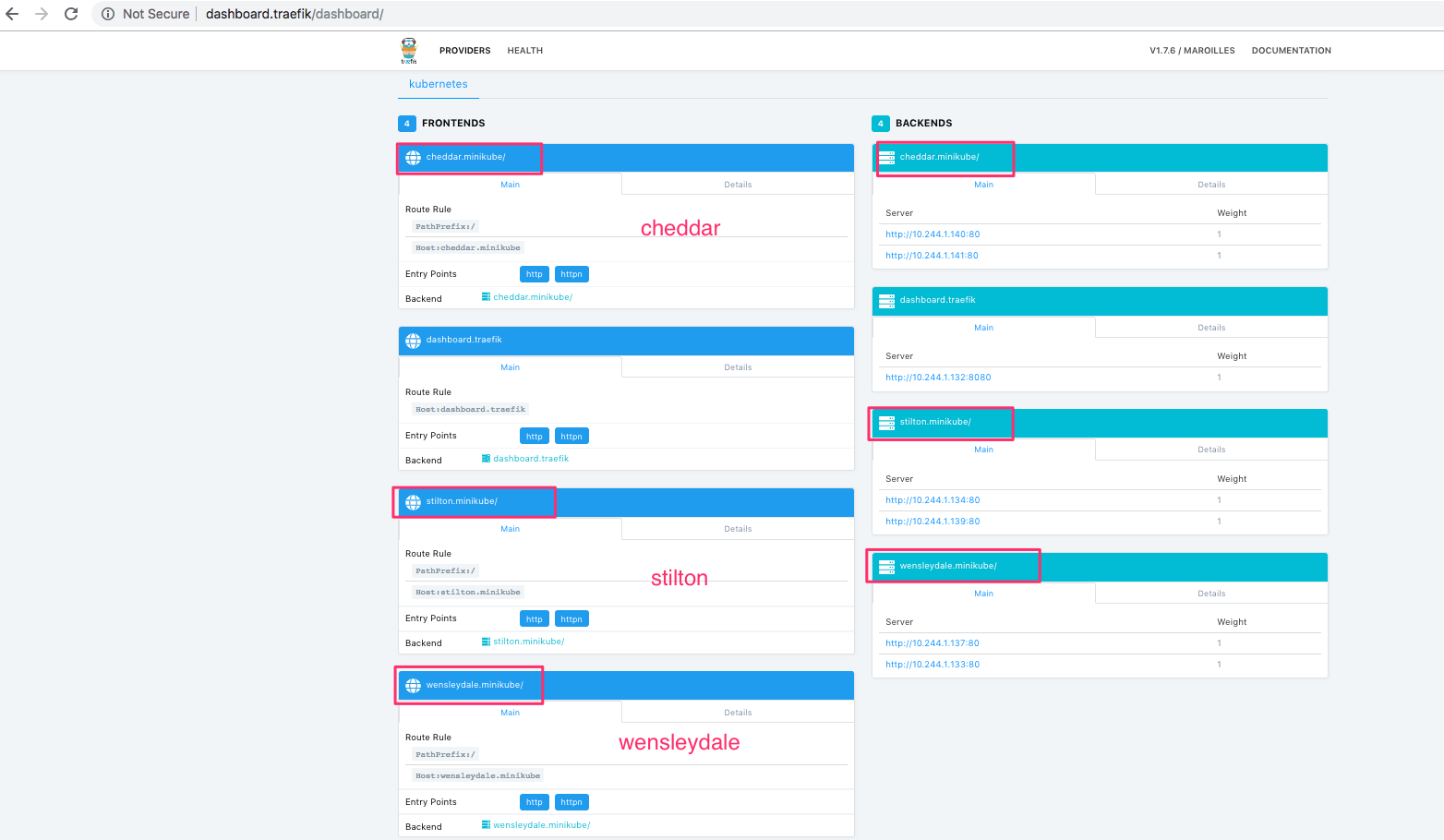
Open the webbrowser and start eating your faviourite cheese
What is PATH based routing
Path based routing differ from Name based routing in a sense, we don't have multiple domains names, all the URI is distinguished and routed from the PATH prefix under a single domain, for example the above cheese application can be access through the single URI.
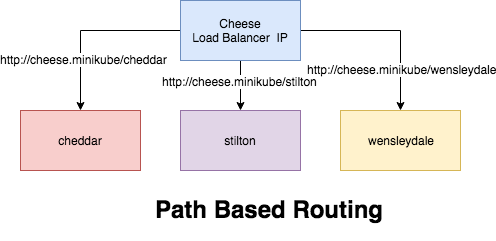
Let's create the PATH base routing for the cheese application
root@kube-master:/home/ansible# kubectl apply -f https://raw.githubusercontent.com/containous/traefik/master/examples/k8s/cheeses-ingress.yaml
ingress.extensions/cheeses created
View the Ingress, as you can notices the newly created ingress cheeses can be accessed through the hostname cheeses.minikube
root@kube-master:/home/ansible# kubectl get ingress
NAME HOSTS ADDRESS PORTS AGE
cheese stilton.minikube,cheddar.minikube,wensleydale.minikube 80 13m
cheeses cheeses.minikube 80 1m
You should now be able to visit the websites in your browser.
Final Note
- The above traefik installation is not secure, and shouldn't be used for production, for production setting refer the helm stable/trafeik charts, for example the below chart value will set traefik in SSL mode, and set the BASIC AUTH enabled
helm install stable/traefik --name traefik --set dashboard.enabled=true,dashboard.domain=dashboard.traefik,rbac.enabled=true,dashboard.auth.basic.traefik='$apr1$vUmd7ddA$CoklUZpHBbRzvnZUz6eFY.',ssl.enabled=true,ssl.enforced=true --namespace kube-system
- It is advisable to install the traefik in the kube-system namespace
- Always measure your resource needs, and adjust requests and limits accordingly.
Thanks Happy traefiking, do poke me for any problems
Video Demo
Thanku for reading !!! Give a Share for Support
Your Support Matters!
Instead of directly asking for donations, I'm thrilled to offer you all nine of my books for just $9 on leanpub By grabbing this bundle you not only help cover my coffee, beer, and Amazon bills but also play a crucial role in advancing and refining this project. Your contribution is indispensable, and I'm genuinely grateful for your involvement in this journey!
Any private key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen, for extra security run this software on your network, no cloud dependency
Kubernetes Related Topics
Linux Related Topics
Ansible Related Topics
Openstack Articles
Applied Cryptography Topics
Web Crypto API Topics
python Cryptography Topics
PHP Cryptography Topics
Topics
For Coffee/ Beer/ Amazon Bill and further development of the project Support by Purchasing, The Modern Cryptography CookBook for Just $9 Coupon Price
Kubernetes for DevOps
Hello Dockerfile